For the latest updates and improvements, see the latest Cloud documentation instead.
Security Monitor#
This feature is only available on paid plans
The Security Monitor provides an overview of all security issues that Codacy found on your repository, and also warns you if any security code patterns are currently turned off.
By default, the page displays the overview for the main branch of your repository but if you have more than one branch enabled you can use the drop-down list at the top of the page to display information for other branches.
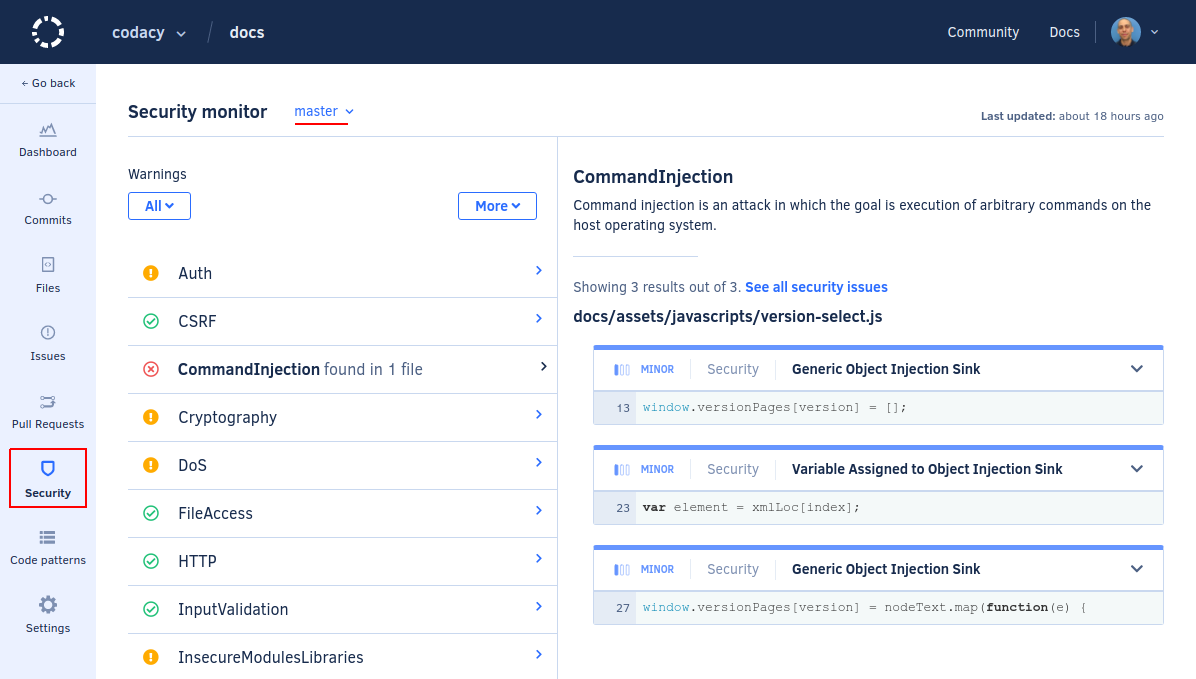
The left-hand side of the dashboard lists the status for each security category that the tools that can analyze the programming languages in your repository support:
| Status | Description |
|---|---|
 |
Codacy found security issues in this category Click the category name to see the list of security issues in this category, and click the title of the issues to see more information about the issue. |
 |
There are security code patterns in this category that are turned off You should turn on the code patterns in this category so that Codacy can find the corresponding security issues. Click the category name to see the code patterns that are turned off, and click the check box next to each code pattern to turn it on. To turn on all security code patterns on the repository regardless of their category, click the button More and select Turn on all security patterns. |
| Codacy can't determine if all security code patterns in this category are turned on or not This happens when you're using configuration files to control which code patterns are turned on. Ensure that you manually turn on the listed code patterns on your configuration files. |
|
 |
Everything is OK for this category All security code patterns in this category are turned on, and Codacy didn't find security issues in this category. |
Tip
You can use the Warnings drop-down list to display only security categories that have found issues or categories that have code patterns turned off.
Supported languages#
The Security Monitor is available for the following languages:
- Apex
- C#
- Java
- JavaScript
- Python
- Ruby
- Scala
- PHP
- C
- C++
- Shell script
- Dockerfile
- Visual Basic
- Elixir
- PowerShell
- TSQL
- Groovy
Tools#
The Security Monitor displays issues using security patterns from:
- Bandit
- Brakeman
- Codacy Scalameta Pro
- ESLint (also: 1, 2, 3 and 4)
- SpotBugs (includes the plugin Find Security Bugs)
- Sonar C#
- Sonar VB.NET
- PMD
- PHP Mess Detector
- Pylint (Python 2)
- Pylint (Python 3)
- RuboCop
- Cppcheck
- ShellCheck
- PHP_CodeSniffer
- Hadolint
- Prospector
- bundler-audit
- Credo
- Flawfinder
- PSScriptAnalyzer
- TSQLLint
- CodeNarc
Supported security categories#
Each issue reported on the Security Monitor belongs to one of the following security categories:
| Security category | Description |
|---|---|
| Android | Android-specific issues. |
| Auth | Authentication is present in almost all web applications nowadays. |
| Command injection | Command injection is an attack in which the goal is the execution of arbitrary commands on the host operating system. |
| Cookies | An HTTP cookie is a small piece of data sent from a website and stored on the user's computer by the browser while the user is browsing. |
| Cryptography | Cryptography is a security technique widely used and there are several cryptographic functions, but not all of them are secure. |
| CSRF | Cross-Site Request Forgery (CSRF) is an attack that forces an end user to execute unwanted actions on a web application in which they're currently authenticated. |
| DoS | The Denial of Service (DoS) attack is focused on making a resource (site, application, server) unavailable for the purpose it was designed. |
| File access | An attacker may use special paths to access files that shouldn't be accessible. |
| Firefox OS | Sensitive APIs of Firefox OS. |
| HTTP | HTTP headers are a common attack vector for malign users. |
| Input validation | Input not validated may originate SQL Injection attacks for instance. |
| Insecure modules/libraries | Consider possible security implications associated with some modules. |
| Insecure storage | Storing sensitive data using these APIs isn't safe. |
| Malicious code | Exposed internal APIs can be accessed or changed by malicious code or by accident from another package. |
| Mass assignment | Mass assignment is a feature of Rails which allows an application to create a record from the values of a hash. |
| Regex | Regex can be used in a Denial of Service attack, that exploits the fact that most Regular Expression implementations may reach heavy computation situations that cause them to work very slowly (exponentially related to input size). |
| Routes | Badly configured routes can give unintended access to an attacker. |
| SQL injection | A SQL injection attack consists of insertion or "injection" of a SQL query via the input data from the client to the application. |
| SSL | Simply using SSL isn't enough to ensure the data you're sending is secure. Man in the middle attacks are well known and widely used. |
| Unexpected behaviour | Assigning values to private APIs might lead to unexpected behavior. |
| Visibility | Fields shouldn't have public accessibility. |
| XSS | XSS enables attackers to inject client-side scripts into web pages viewed by other users. |
| Other | Other language-specific security issues. |
See also#
Share your feedback 📢
Did this page help you?
Thanks for the feedback! Is there anything else you'd like to tell us about this page?
255 characters left
We're sorry to hear that. Please let us know what we can improve:
255 characters left
Alternatively, you can create a more detailed issue on our GitHub repository.
Thanks for helping improve the Codacy documentation.
If you have a question or need help please contact support@codacy.com.